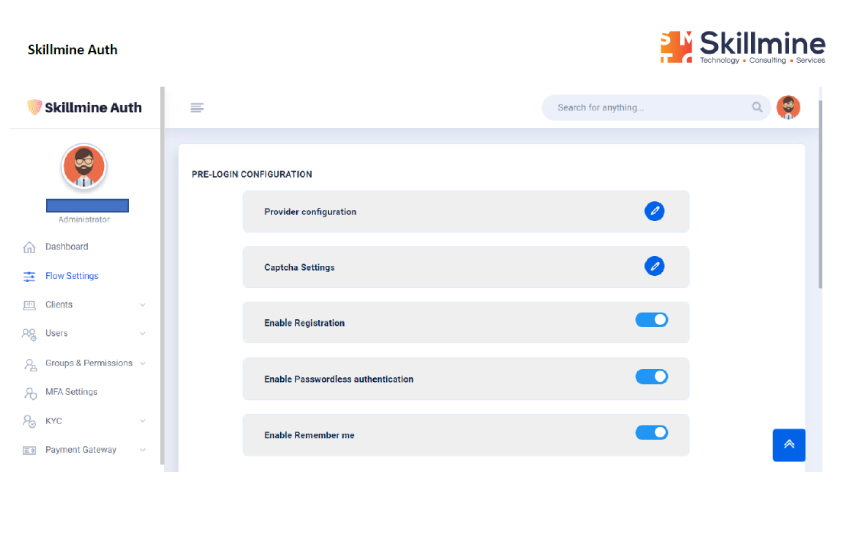
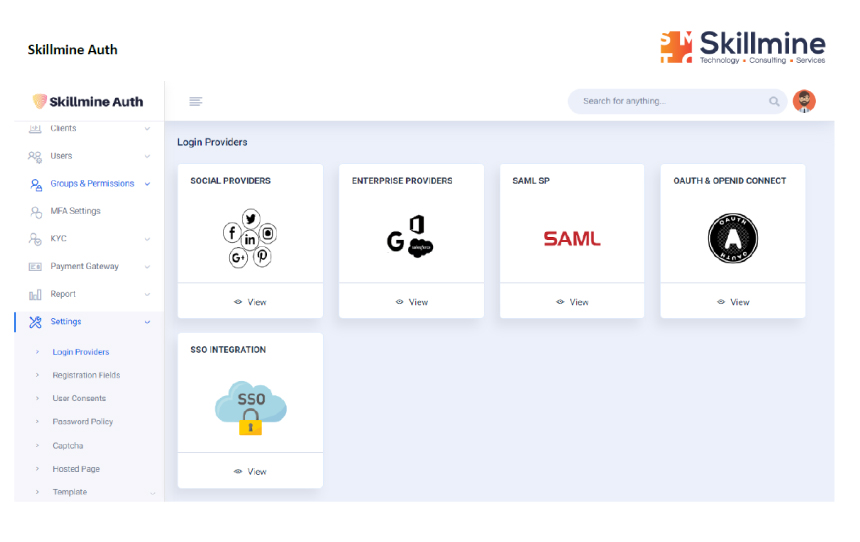
Auth can effortlessly accommodate a multitude of login methods across all the platforms.
Auth can integrate with diverse applications within a multi-cloud environment, enhancing flexibility.
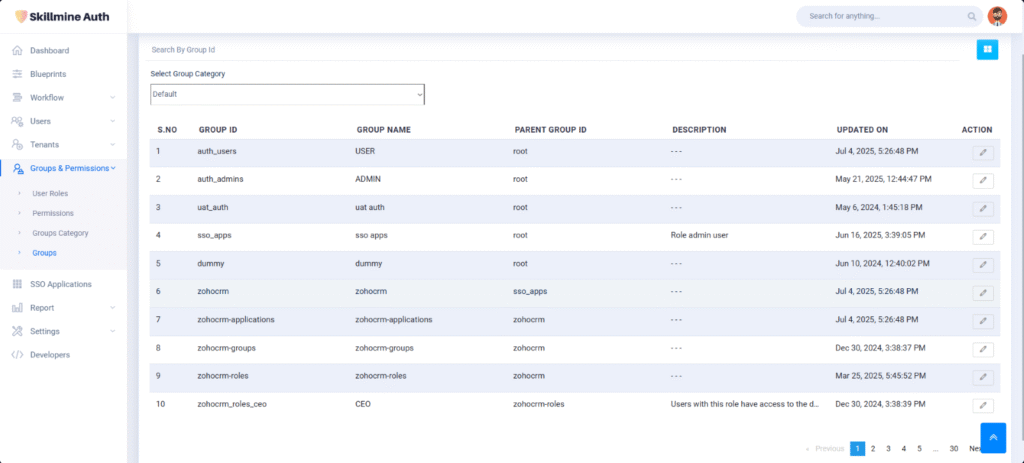
Auth can seamlessly navigate diverse authentication and authorization protocols available.
Skillmine Auth’s Time-Based Access Control feature allows organizations to automate and enforce access permissions based on operational hours, ensuring that critical systems are only available when necessary. This capability helps mitigate risks by restricting access during non-operational hours, such as nights, weekends, or holidays, regardless of the industry. In production environments, shift-based access can be enforced, enabling only on-duty personnel to interact with machinery or applications. Knowledge-based institutions can use this feature to align access with scheduled sessions or exams, while any regulated industry can maintain strict control over when sensitive data or applications are accessible—ultimately enhancing both security and compliance.
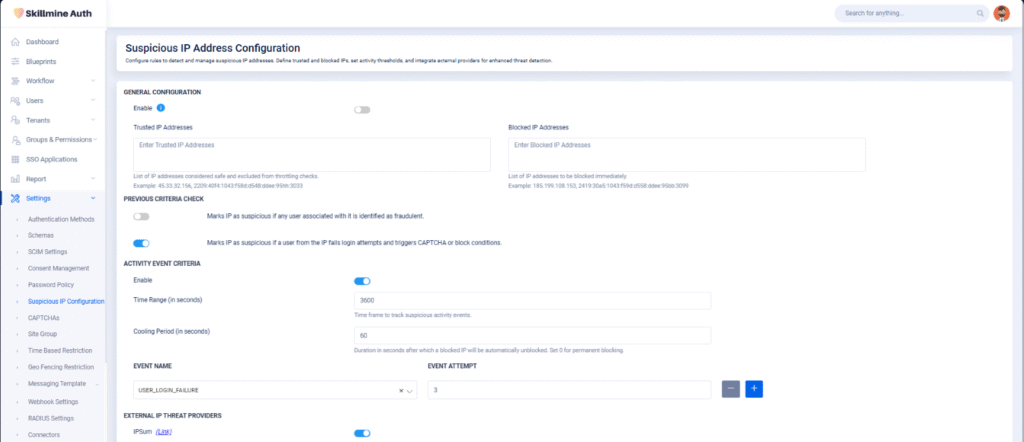
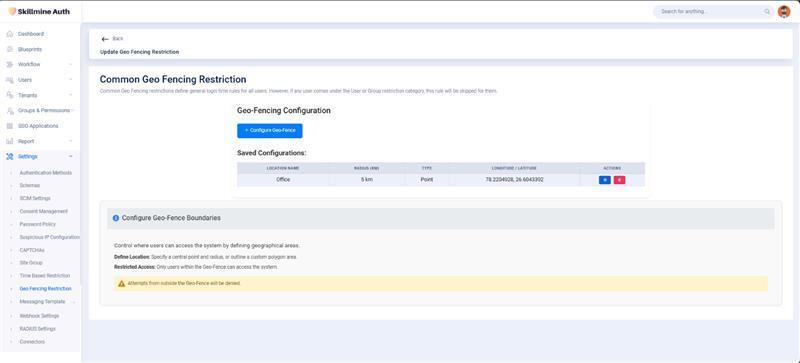
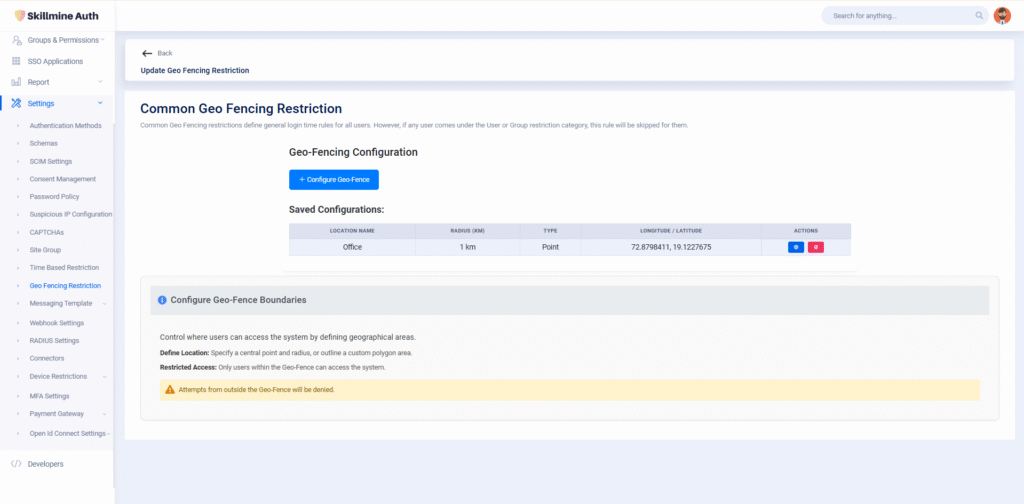
Geo-location-based access controls within Skillmine Auth allow enterprises to implement contextual access boundaries based on user geography. Using IP-derived location intelligence, organizations can restrict logins to trusted areas such as corporate campuses, approved branches, or known service regions—while simultaneously blocking access from risky or irrelevant territories. This helps in upholding data residency requirements, enforcing localized compliance, and reducing exposure to international threats. Industries ranging from healthcare to fintech can tailor geo-access policies to safeguard information without hindering legitimate access from remote or mobile teams.
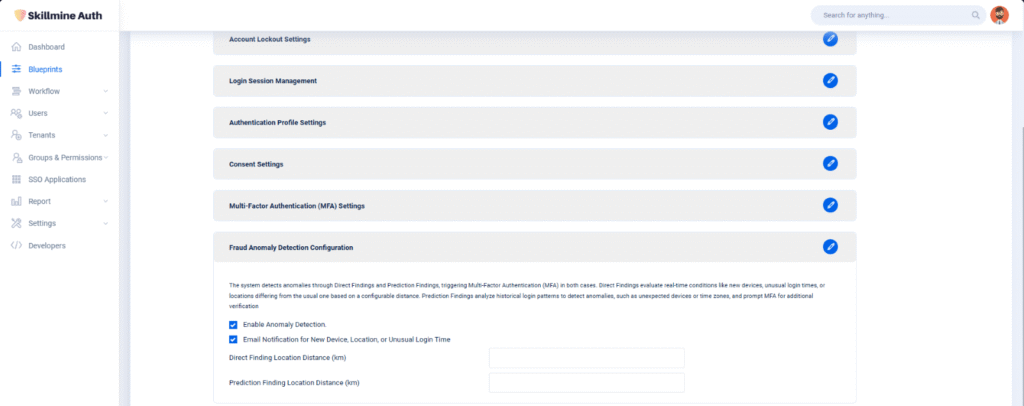
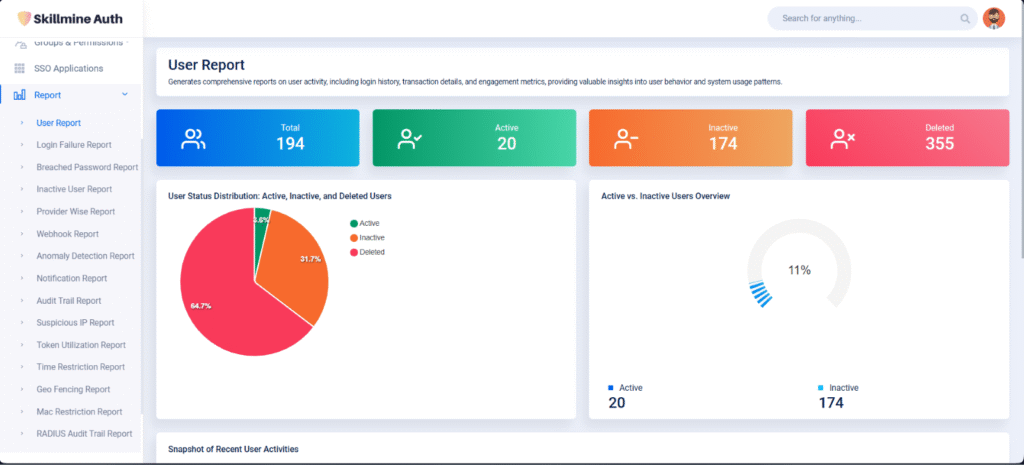
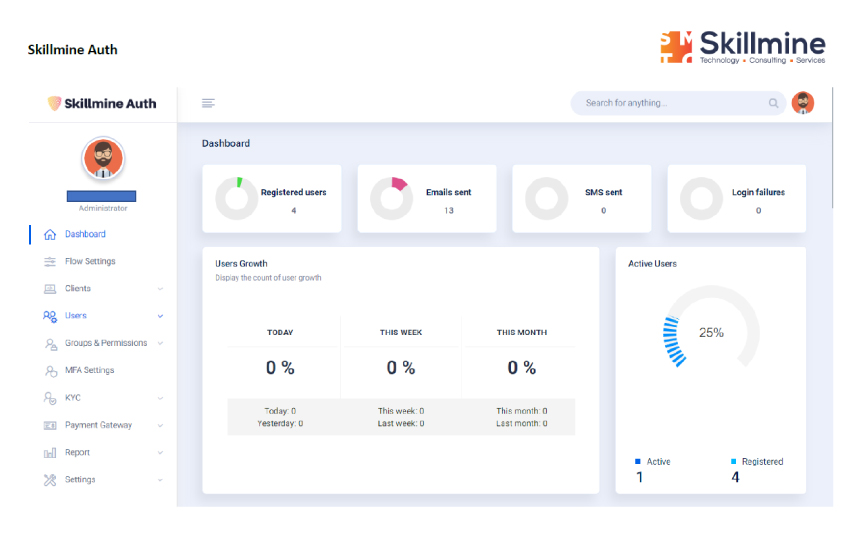
Skillmine Auth is a purpose-built platform that redefines access management for industries with diverse operational demands. Its comprehensive suite of features—ranging from MFA and Role-Based Access to Anomaly Detection and IP Protection—empowers organizations to create secure, efficient, and compliant digital ecosystems. From protecting clinical data in hospitals to managing access to factory systems, customer platforms, or government networks, Skillmine Auth delivers reliable security and seamless user experience. Designed for adaptability and built with privacy in mind, it enables enterprises to future-proof their identity strategy across sectors.
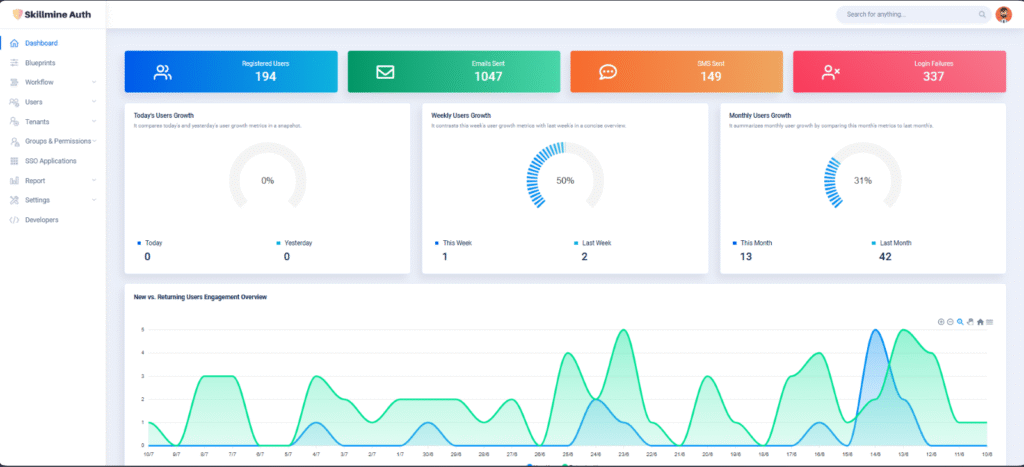
Geo-location-based access controls within Skillmine Auth allow enterprises to implement contextual access boundaries based on user geography. Using IP-derived location intelligence, organizations can restrict logins to trusted areas such as corporate campuses, approved branches, or known service regions—while simultaneously blocking access from risky or irrelevant territories.

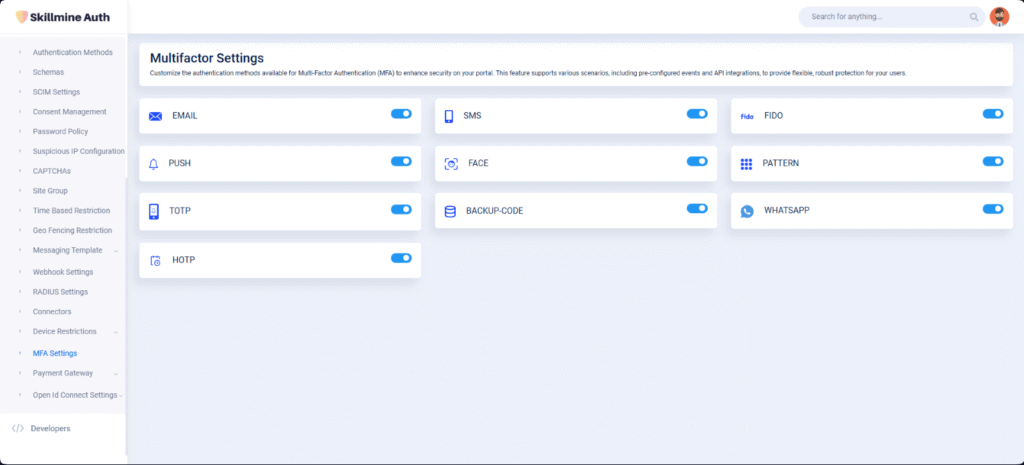
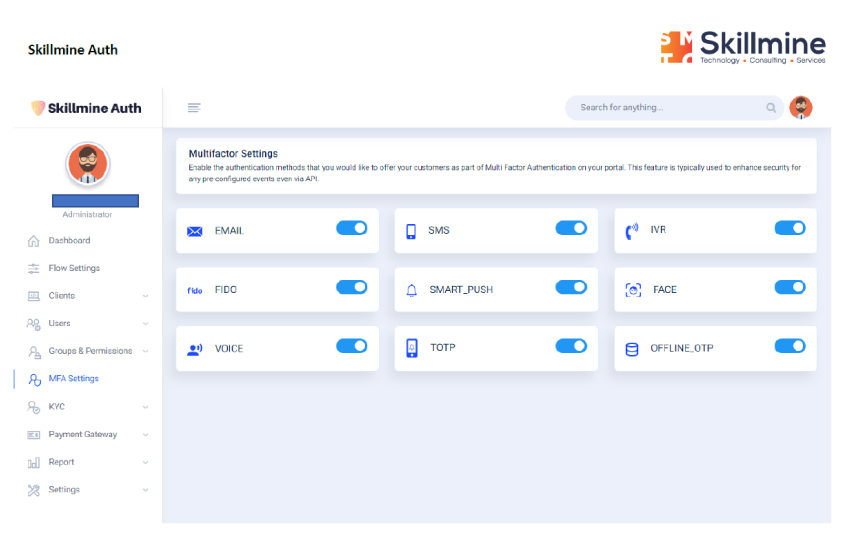
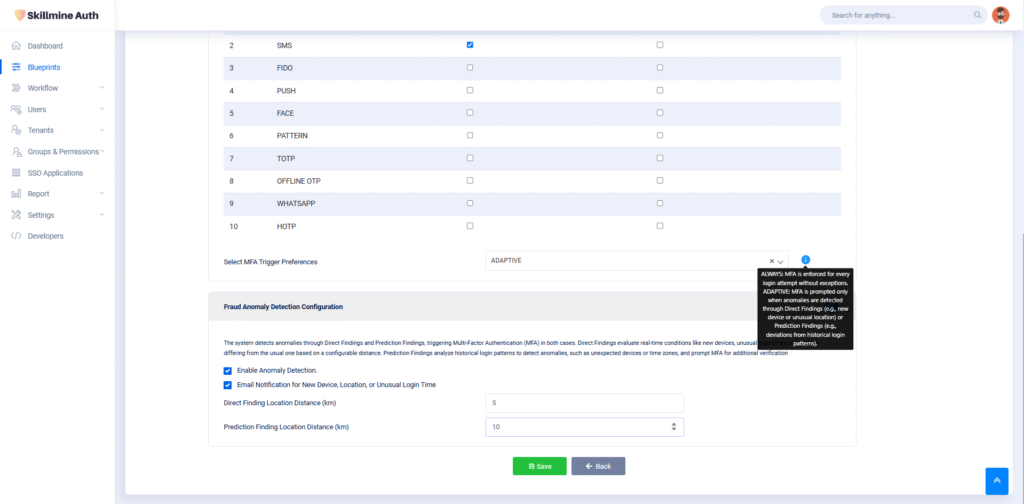
Skillmine Auth’s adaptive MFA adjusts security dynamically—adding layers of verification based on risk conditions like unknown devices or locations, providing frictionless yet secure login.

Geo-location-based access controls within Skillmine Auth allow enterprises to implement contextual access boundaries based on user geography...

Skillmine Auth’s adaptive MFA adjusts security dynamically—adding layers of verification based on risk conditions...


| Stage | What Happens | How Connectors Help |
|---|---|---|
| Onboarding | New user joins the organization | Automatically creates the user across relevant apps |
| Access Changes | Role/policy changes during employment | Instantly updates user permissions, groups, and roles |
| Offboarding | User leaves or shifts department | Removes access from all connected systems to avoid security risks |
Skillmine Auth integrates with 50+ enterprise and cloud systems—easily connect apps, tools, and infrastructure in just a few clicks.

Salesforce

Zoho CRM

Pipedrive

Microsoft 365

Keycloak

Google Workspace

Azure AD

AWS IAM

Bamboo HR

Zoho People

HRone

Greyt HR

Adrenalin Max

Atlassian

Trello
Tableau

Zoom

ManageEngine

Freshdesk

Fresh Service

Zendesk

Splunk

Elastic Search

Datadog

Sumo

Logz.io